Encryption tools for MEV Protection in DeFi
Source : https://www.youtube.com/watch?v=caNBYKXWj-A

The original speaker for this talk had to cancel last minute due to an unexpected flight cancellation. As a result, Liam McDonald is presenting in their place
Fairblock is developing cryptographic tools for programmable privacy and bad MEV prevention in DeFi.
However, bad MEV prevention is just one small application of their broader technology for on-chain programmable privacy using advanced cryptography like Fully Homomorphic Encryption and Zero Knowledge Proofs.
The presentation will cover :
- The current state of MEV
- What is Fairblock and their architecture using threshold Identity-based encryption (IBE)
- Applications of IBE in DeFi like encrypted intents, sealed bid auctions, and generalized programmable privacy
- Exciting things that can be built with this programmable privacy
- What to expect from Fairblock in the next year
The current state of MEV (3:30)
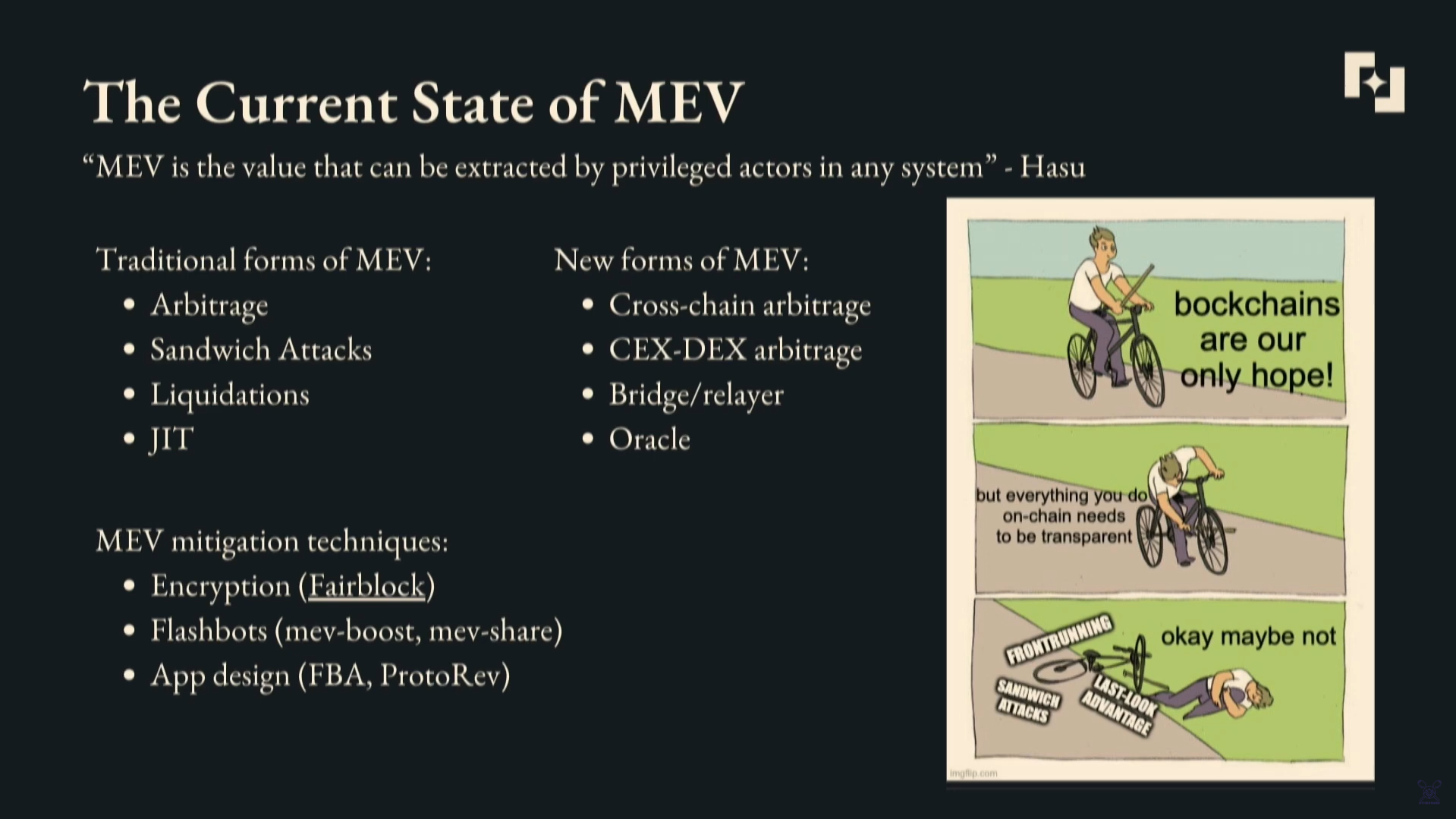
MEV refers to the value that privileged actors can extract from a system. Traditional forms of MEV include arbitrage, sandwich attacks, liquidations, and just-in-time attacks.
Newer forms of MEV emerge from cross-chain arbitrage, DEX-to-DEX arbitrage, and opportunities at the bridge and oracle levels.
There are some mitigation techniques available:
- Encryption solutions like Fairblock is working on to prevent bad MEV specifically.
- Flashbots with MEV-Boost and MEV-Share.
- Design solutions like frequent batch auctions and protorev.
Fairblock's cryptographic tools focus on preventing bad MEV opportunities, not enabling good MEV.
What is fairblock ? (4:50)
Fairblock provides programmable privacy infrastructure and applications for blockchain protocols and apps. Their goal is to protect users from malicious actors and the downsides of on-chain transparency.
They believe the current lack of privacy in blockchain is a major barrier to adoption. Most apps are limited to a global user base due to no privacy.
Existing on-chain privacy is isolated in siloed Layer 1s, positioning privacy as a luxury rather than a standard.
Instead, Fairblock wants to make privacy accessible within users' favorite ecosystems and apps, without sacrificing UX. So they built FairyRing.
Introduction to FairyRing (6:40)
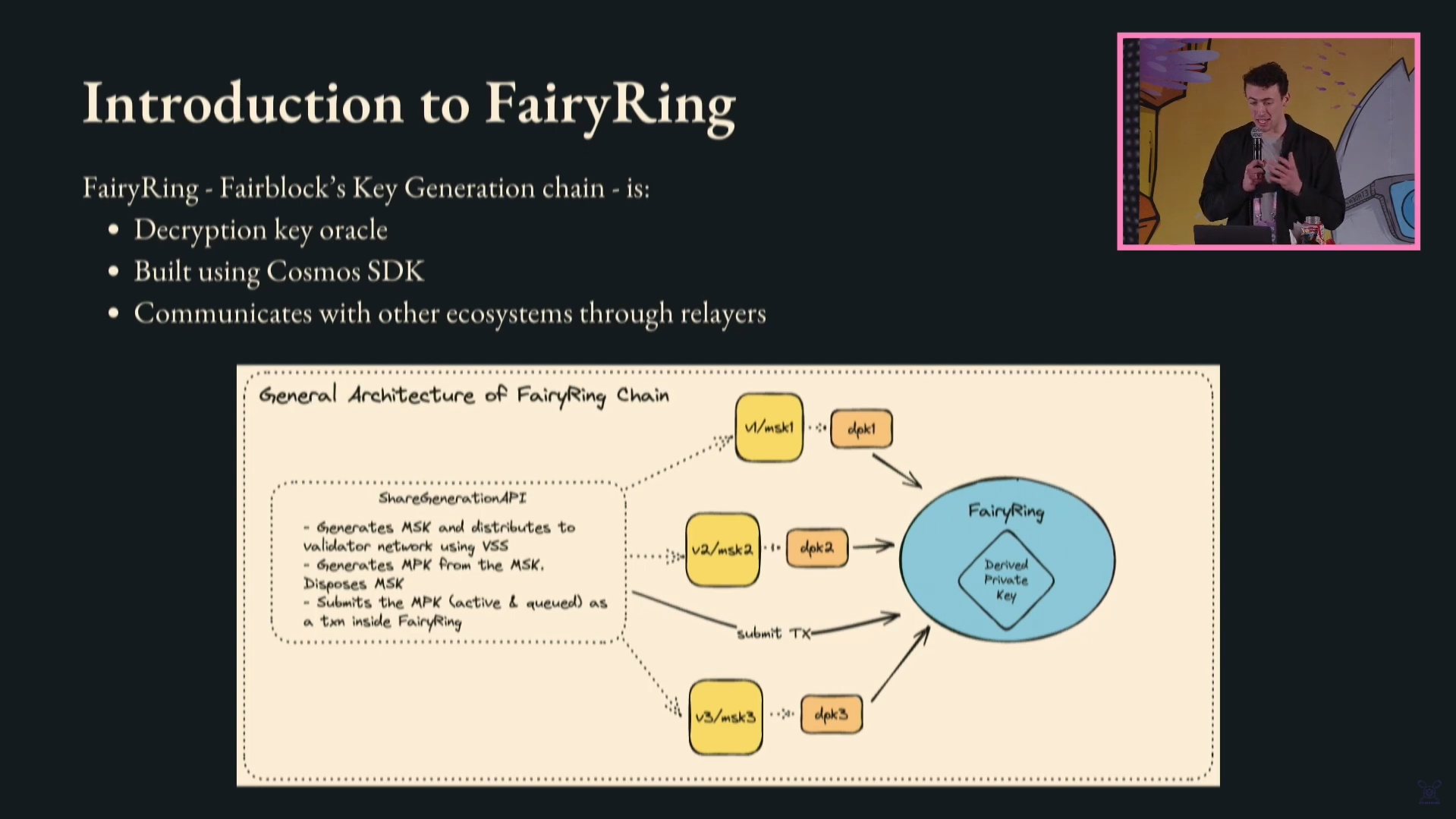
FairyRing is a key generation chain that acts as a decryption oracle, sending encryption/decryption keys to any blockchain or app.
FairyRing is a cosmos SDK chain, and uses IBC or a network of relayers called Fairyport to connect to other chains.
How it works:
- Users encrypt a transaction with a condition for decryption (e.g. block height, asset price, ZKP, etc).
- The encrypted transaction is committed on-chain and waits in the mempool.
- When the condition is met, FairyRing validators are notified via Fairyport.
- Validators derive their share of the private key locally first.
- They submit their share to FairyRing.
- Once a threshold of shares is reached, FairyRing constructs the full private key.
- FairyRing sends the key to the destination chain.
- The transaction is decrypted and executed.
Threshold Identity-based encryption (9:00)
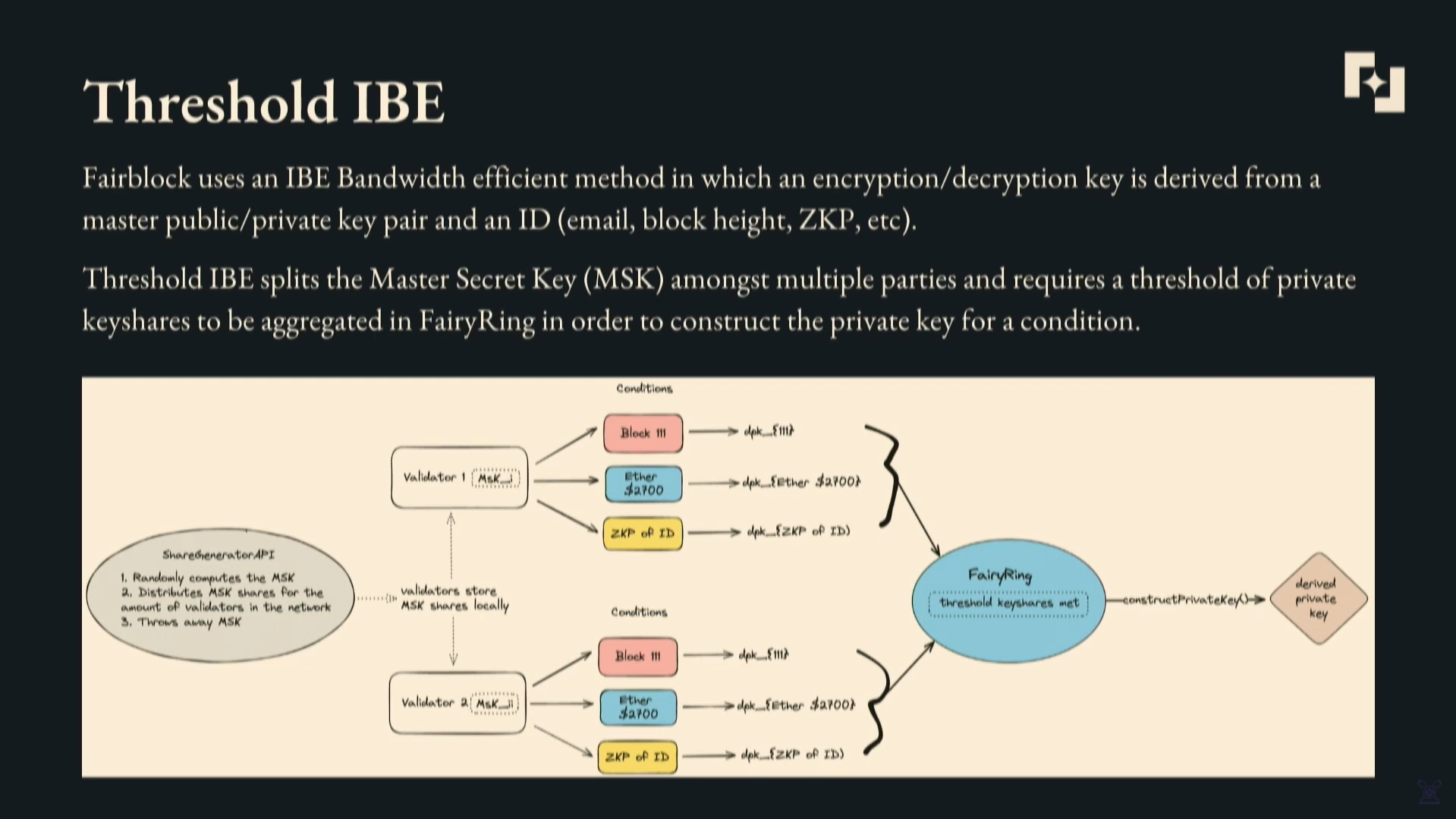
FairyRing uses a cryptographic technique called threshold identity-based encryption (IBE). This allows specifying conditions for decrypting transactions on-chain.
How threshold IBE works on FairyRing currently:
- A master secret key (MSK) is generated from an API. This will soon be generated collaboratively by validators via a DKG)
- The MSK is split into shares and distributed to FairyRing validators. When an on-chain decryption condition is met, validators generate their private key share locally. They submit their share to FairyRing.
- FairyRing constructs the full private key from the threshold of shares.
- FairyRing sends the key to decrypt the transaction on the destination chain.
So in summary, FairyRing uses distributed key generation and threshold reconstruction to derive conditional decryption keys for encrypted transactions across chains.
Encrypted intents (10:25)
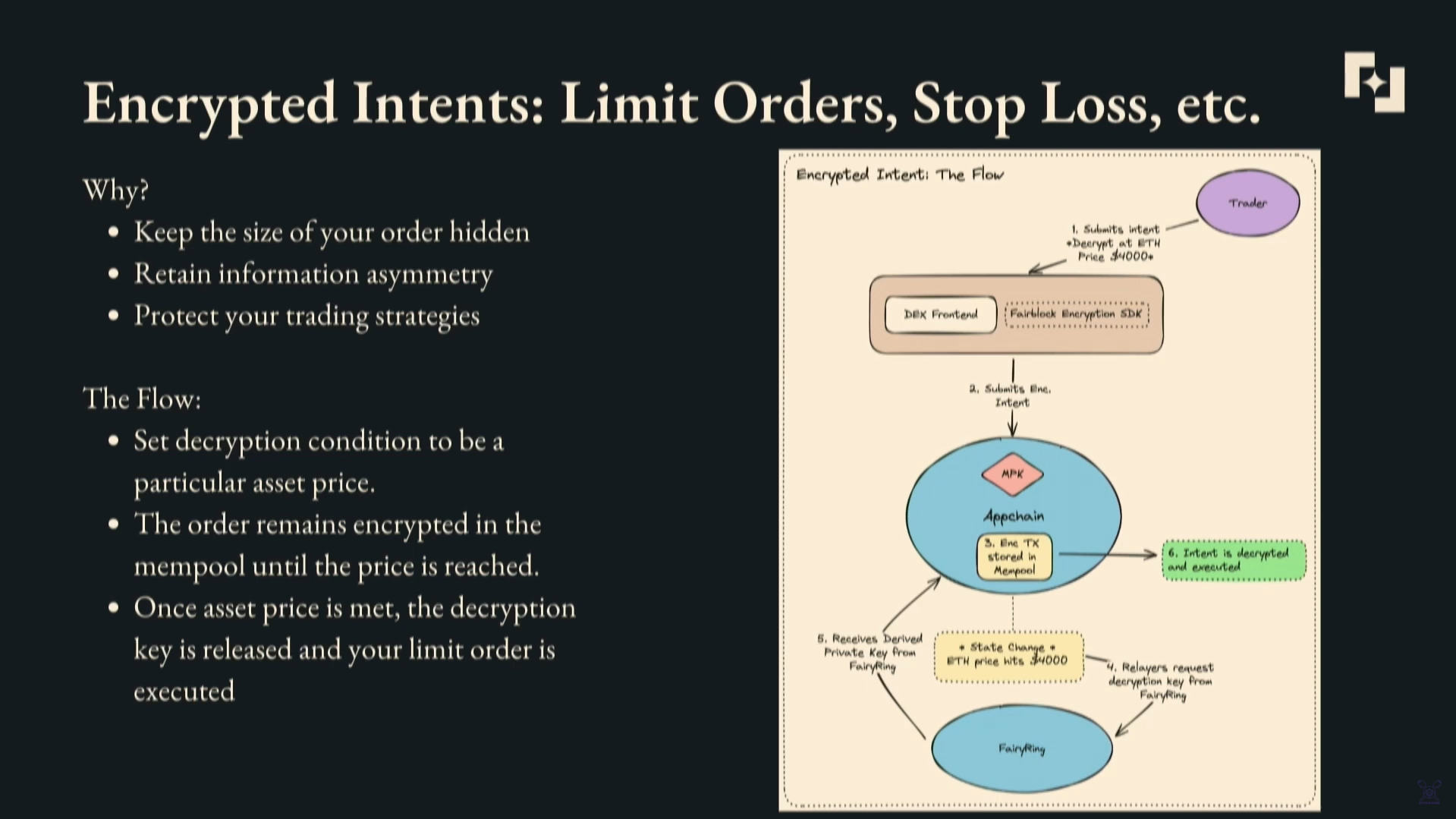
Encrypted intents refer to encrypted limit orders, stop losses, or other programmable trading transactions in DeFi.
How it works:
- Trader submits an encrypted intent conditioned on something like ETH price
- The app frontend routes it to the blockchain.
- It waits encrypted in the mempool.
- When the condition is met (i.e. ETH hits $4k), FairyRing is notified.
- FairyRing generates the decryption key and sends it to the app chain.
- The intent is decrypted and executed.
Encrypted programmable intents allow traders to keep orders private until predefined conditions are met on-chain, at which point FairyRing provides the decryption key.
This prevents front-running and protects trading strategies, while retaining programmable execution based on market conditions.
Sealed-Bid Auctions (12:50)
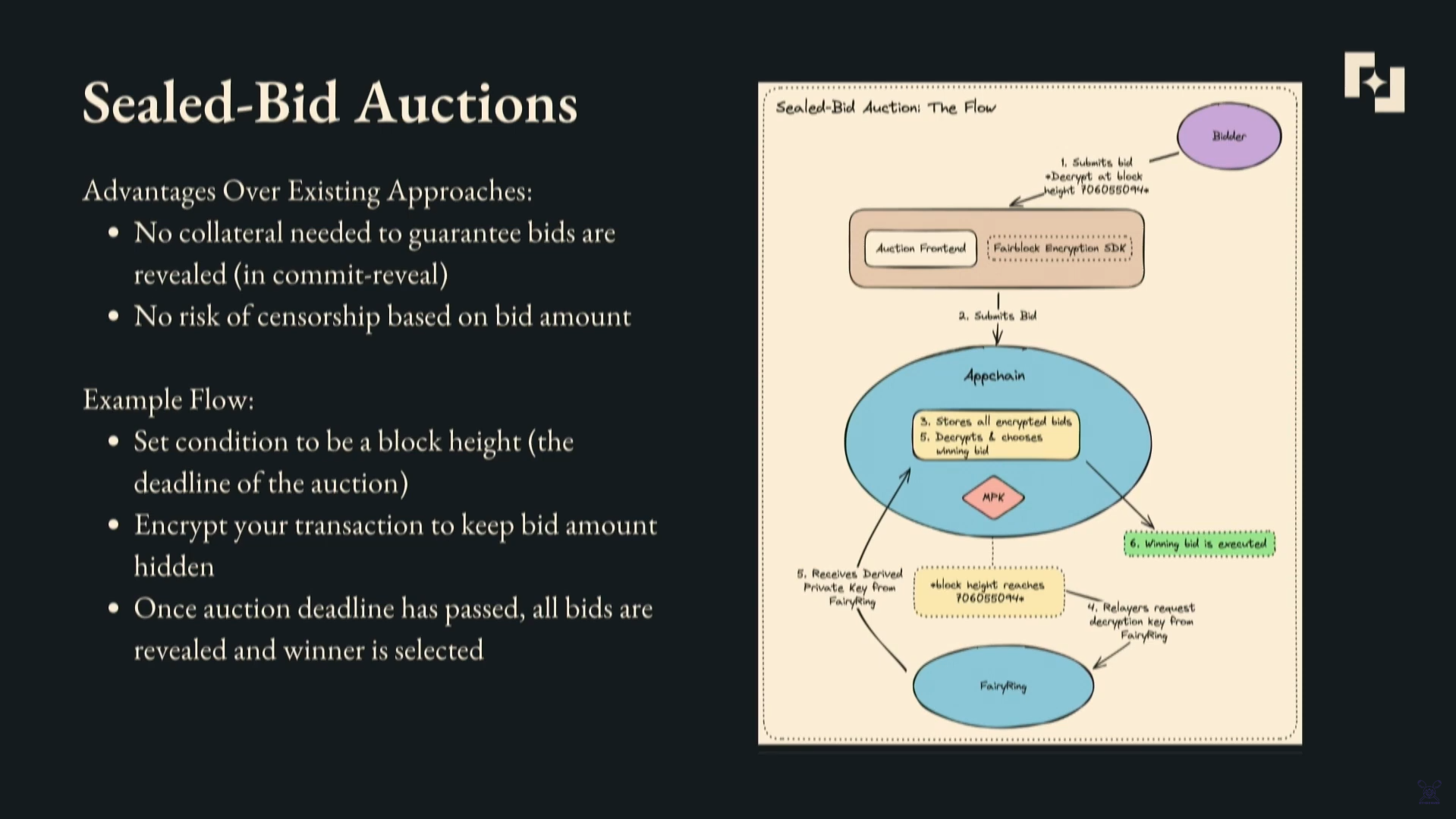
Sealed bid auctions involve bidders submitting encrypted bids that are only revealed at the end of the auction.
How it works :
- Bidders encrypt their bid conditioned on a future block height (the auction end).
- The encrypted bids sit in the mempool until the end block is reached.
- At the end, FairyRing provides the decryption keys to the app chain.
- The chain decrypts all bids and executes the winning bid's logic.
Threshold IBE allows conducting sealed bid auctions on-chain where bids remain encrypted until simultaneously revealed at the end.
Advantages over traditional commit-reveal auctions :
- No collateral needed to guarantee bid reveal.
- No risk of censorship based on bid amount since encrypted.
Conditional Decryption (14:45)
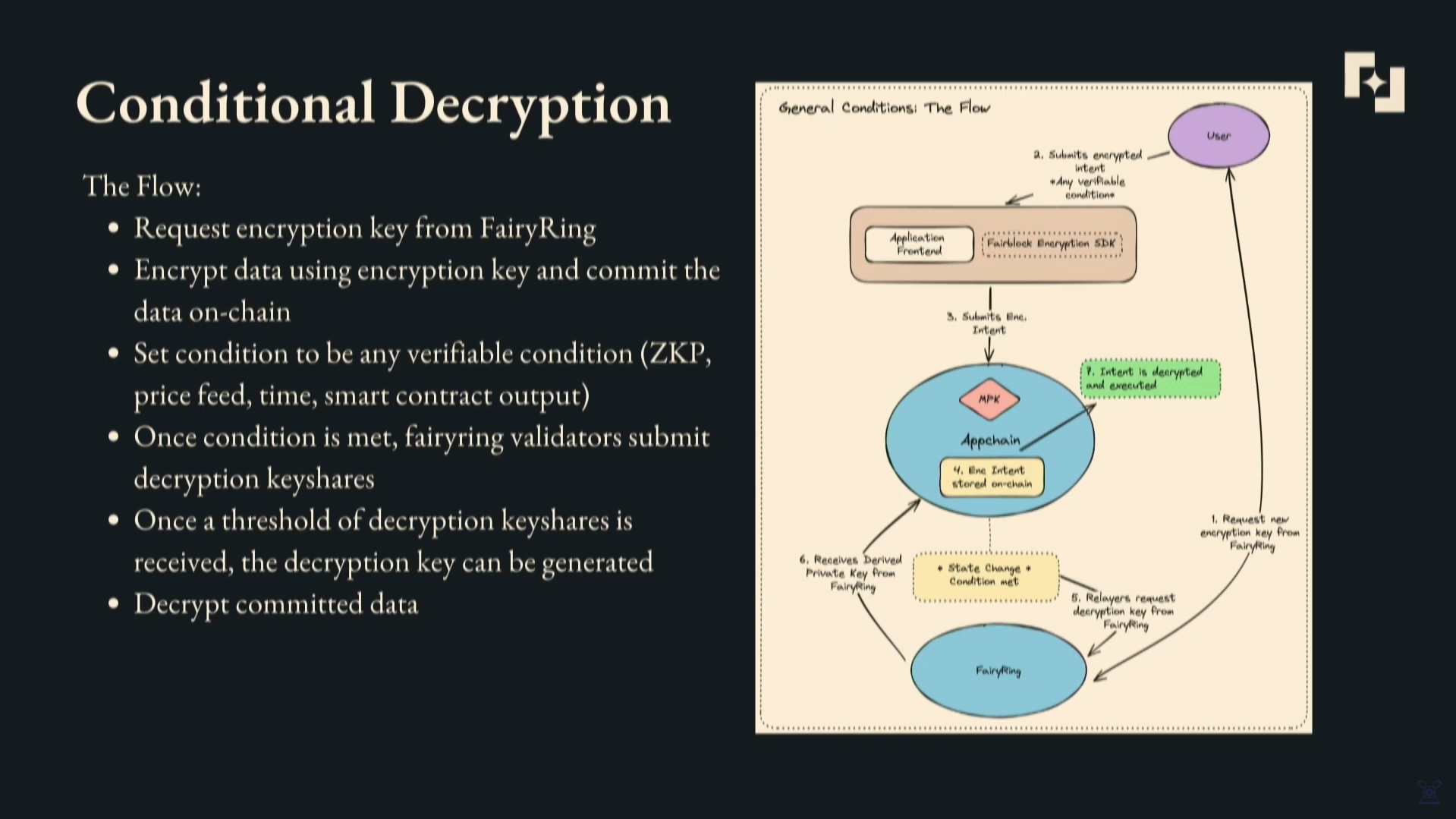
The conditional decryption and programmable privacy enabled by threshold IBE can be applied to any on-chain application, not just DeFi :
- FairyRing sends a master public key (MPK) to the app chain initially.
- Users choose a decryption condition and match it to the MPK to generate the public key for their encrypted transaction.
- The encrypted transaction sits in the mempool until the condition is met.
- FairyRing provides the decryption key to the app chain.
- The transaction is decrypted and executed.
The potential use cases include private governance, gaming, and more.
Cool things to build (16:00)

Threshold IBE unlocks many new design spaces for on-chain applications with programmable privacy :
- Private governance - Fairblock has already built this for Cosmos Hub
- Encrypted on-chain intents and orders
- Randomness generation for gaming, gambling, etc.
- Censorship resistant shared sequencing by decrypting at the sequencer level
- Encrypted mempools
- Privacy preserving rollups
- Private on-chain games
...And maybe other use cases we haven't discovered yet
Programmable privacy greatly expands what can be built on-chain while retaining flexibility via conditional decryption This will unlock the next generation of apps attracting new users
Looking for updates (17:35)

- QR Code leads to Fairblock's Linktree
- The testnet launch is scheduled on March 6
- Hackathon soon to be announced
- Partnerships with other blockchain infrastructure and layer 2s
- There will be opportunities for builders to contribute to their project early on.